Contact Us
Email: info@mohitdesigns.com
Mobile: +91-9718991639
Contact Us
Email: info@mohitdesigns.com
Mobile: +91-9718991639

A Cache Poisoning Attack is a serious security threat that targets web applications by injecting malicious content into a caching system. This type of attack can lead to compromised data, altered responses to legitimate requests, and even denial of service. Understanding how this attack works is crucial to securing your web applications and protecting your users from malicious activity.
In this article, we’ll explore the mechanics of cache poisoning, examine real-world examples, and provide actionable tips to prevent this attack from affecting your web systems.
A web cache is a mechanism used to temporarily store (or “cache”) web content, such as HTML pages, images, and files, so that they can be quickly served to users upon subsequent requests. Instead of fetching the requested data from the origin server every time, the cache delivers a stored version, significantly reducing server load, bandwidth usage, and latency.
Web caches can exist in various locations, such as browsers, CDN (Content Delivery Network) servers, or proxy servers. The main benefit is improving performance and reducing response times for end users.
Web caching operates based on the principle of storing and reusing frequently accessed resources. When a user makes a request to a website, the server checks if the requested content is already stored in the cache. If the content is available (known as a “cache hit”), the cached response is served, speeding up the loading process. If not (a “cache miss”), the request is forwarded to the origin server, and the content is then stored in the cache for future use.
Here’s a breakdown of the web caching process:
Cache poisoning occurs when an attacker injects malicious data into a cache server, which is then served to unsuspecting users. Caches store responses from servers to reduce load times and improve performance. When an attacker successfully manipulates the cache, it causes users to receive altered or harmful responses, instead of legitimate ones.
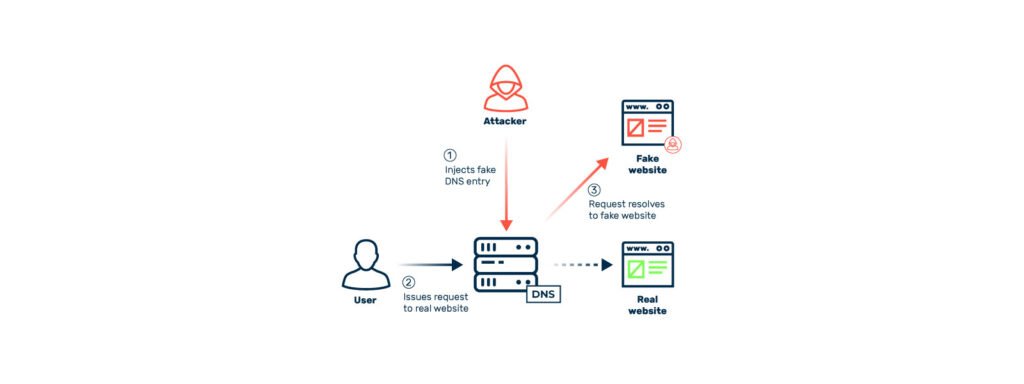
Here’s how a typical cache poisoning attack unfolds:
Real-World Example:
Consider a scenario where a web application caches HTTP responses based on URL parameters. An attacker could inject a malicious script by manipulating these parameters, and when users access the same page, the poisoned response with the malicious script is served to them.
To prevent a cache poisoning attack, developers and system administrators must implement multiple layers of defense. Here are some key strategies:
Cache-Control and Pragma. This prevents caching sensitive data, ensuring that only safe responses are stored.Cache poisoning attacks can have devastating effects on both web application performance and user trust. By understanding how these attacks work and implementing preventive measures like sanitizing inputs, using strong cache keys, and configuring proper cache-control headers, you can safeguard your systems against such threats.
Staying vigilant and regularly updating your security measures is crucial to maintaining a secure and reliable caching mechanism in your web applications.