Contact Us
Email: info@mohitdesigns.com
Mobile: +91-9718991639
Contact Us
Email: info@mohitdesigns.com
Mobile: +91-9718991639

In today’s digital landscape, securing user data is no longer optional; it’s essential. As data breaches become more common, encrypting access tokens has emerged as a vital step in safeguarding sensitive information. In this post, we’ll delve into why encrypting access tokens matters, how it works, and how it can reinforce your application’s overall security. We’ll also discuss practical examples to help you understand how token encryption enhances data security.
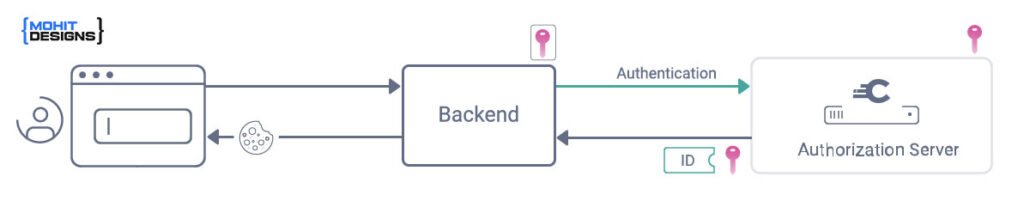
Access tokens are digital keys that allow systems to authenticate a user or application. Think of them like the keys to your home—they grant access to resources and dictate permissions for various users. These tokens are typically used in web applications and APIs to verify identity and control data access. For example, when you log into an application, an access token is often generated and sent back to your device, where it’s used for future authentication requests.
However, while access tokens are critical for managing access, they can also be a security risk if left unprotected. If hackers gain access to these tokens, they can impersonate users, access confidential data, and potentially compromise entire systems.
Encrypting access tokens provides an added layer of security by making them unreadable to unauthorized users. Without encryption, a stolen access token can be used by an attacker to impersonate legitimate users and access restricted data. When tokens are encrypted, however, they become significantly harder to misuse.
Encryption ensures that only trusted parties with the correct decryption key can access the token data. This way, even if someone intercepts an access token, they won’t be able to read or use it without decrypting it first.
Token encryption typically involves two key components: encryption algorithms and encryption keys.
Together, these components ensure that only authorized parties with the correct key can access the original token data.
Imagine a scenario where you have a web application that uses OAuth 2.0 for authentication. When users log in, they receive an access token that allows them to retrieve data from an API. If you store this token in its raw form, it could easily be intercepted by hackers. By encrypting the token before storing it, however, you ensure that any intercepted token remains unreadable.
Let’s consider how you might use AES encryption in JavaScript to protect access tokens:
const crypto = require('crypto');
const algorithm = 'aes-256-cbc'; // Encryption algorithm
const secretKey = crypto.randomBytes(32); // Generate a 32-byte encryption key
const iv = crypto.randomBytes(16); // Initialization vector for encryption
// Function to encrypt the token
function encryptToken(token) {
const cipher = crypto.createCipheriv(algorithm, secretKey, iv);
let encrypted = cipher.update(token, 'utf8', 'hex');
encrypted += cipher.final('hex');
return `${iv.toString('hex')}:${encrypted}`;
}
// Function to decrypt the token
function decryptToken(encryptedToken) {
const [ivHex, encrypted] = encryptedToken.split(':');
const decipher = crypto.createDecipheriv(algorithm, secretKey, Buffer.from(ivHex, 'hex'));
let decrypted = decipher.update(encrypted, 'hex', 'utf8');
decrypted += decipher.final('utf8');
return decrypted;
}
// Usage
const token = 'user-access-token';
const encryptedToken = encryptToken(token);
console.log('Encrypted Token:', encryptedToken);
console.log('Decrypted Token:', decryptToken(encryptedToken));In this code:
encryptToken function encrypts the token using the AES-256 algorithm.secretKey can decrypt.Encrypting access tokens offers multiple advantages that contribute to a stronger security posture:
Adding encryption to access tokens requires some planning. Here are a few steps to help you integrate encryption effectively:
Encrypting access tokens is an essential security move that protects both your users and your application from unauthorized access. While token encryption may seem complex, its benefits far outweigh the initial setup effort. Not only does encryption guard against data theft, but it also ensures compliance and builds trust with users.
If you’re handling sensitive information, don’t wait to make token encryption a priority in your security strategy. By taking these proactive steps, you can confidently protect your users and data, making your application resilient against common security threats.