Contact Us
Email: info@mohitdesigns.com
Mobile: +91-9718991639
Contact Us
Email: info@mohitdesigns.com
Mobile: +91-9718991639


Cyberattacks are becoming more sophisticated every day, targeting unsuspecting users through clever tricks and deceptive tactics. One such attack is clickjacking—a dangerous technique that preys on users’ trust and lack of awareness. This guide will provide an in-depth look at clickjacking, how it works, its consequences, and practical steps to protect yourself.
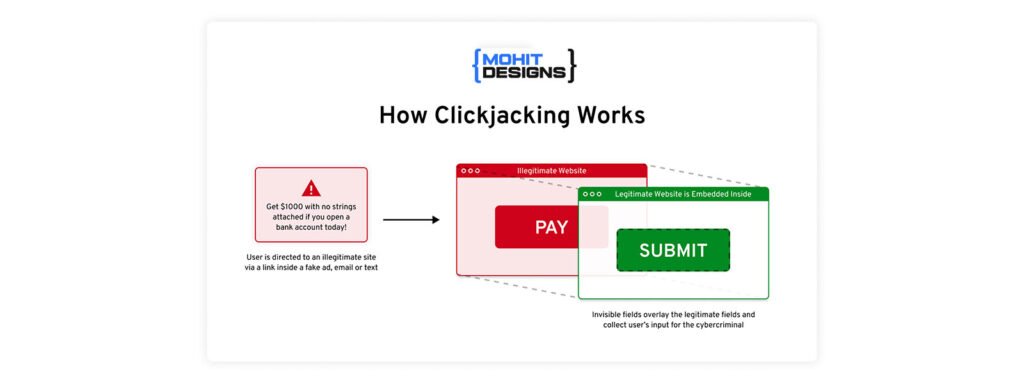
Clickjacking, short for “click hijacking,” is a type of cyberattack where attackers manipulate users into performing actions they didn’t intend. This involves tricking a user into clicking on hidden or disguised elements of a web page.
For example, imagine you’re clicking a button to play a video, but beneath that button, there’s a hidden link that authorizes a payment or grants access to your sensitive data. You think you’ve performed a harmless action, but in reality, you’ve been “hijacked” into doing something potentially harmful.
Clickjacking is often referred to as a User Interface (UI) redress attack because it exploits the design of web interfaces to mislead users.
Clickjacking relies on the layering of web elements to deceive users. Here’s a step-by-step explanation of how attackers execute these attacks:
Attackers may trick users into liking or sharing a malicious post on platforms like Facebook or Twitter. A transparent “Like” button overlays a harmless-looking image or video. As a result, the user unknowingly spreads malicious content, amplifying the attack’s reach.
On a banking or e-commerce website, attackers can overlay a hidden “Submit” button to steal your login credentials or initiate unauthorized transactions.
One common example involves tricking users into granting access to their camera or microphone. A transparent “Allow” button might overlay a game start button, leading users to unknowingly grant access to their devices.
In this scenario, users attempting to view product details or confirm orders might unknowingly authorize a payment or change account settings.
Clickjacking can also lead to users unknowingly downloading malware. A hidden “Download” button might be placed behind a legitimate link, causing unsuspecting users to install harmful software.
The consequences of clickjacking can be far-reaching, including:
To protect yourself from clickjacking attacks, adopt these strategies:
Stick to well-known, reputable websites and avoid clicking on suspicious links or pop-ups. Be cautious when visiting lesser-known platforms.
Modern browsers often have built-in protection against clickjacking, and additional extensions like NoScript or uBlock Origin can provide further safeguards.
Keep your browser updated and enable security features like sandboxing and enhanced security protocols. These can help detect and block malicious content.
Hover over links or buttons to preview the destination URL before clicking. If something seems off, avoid interacting with it.
If you’re a developer, safeguarding your website against clickjacking is crucial. Follow these steps to minimize risks:
The X-Frame-Options HTTP header can prevent your website from being embedded in iframes, which is the backbone of most clickjacking attacks. Use one of the following directives:
DENY: Prevents your page from being embedded by any website.SAMEORIGIN: Allows embedding only by pages from the same domain.Use CSP to define rules about which domains can load content on your website. For example:
Content-Security-Policy: frame-ancestors 'self';Use CAPTCHA or other verification steps to ensure user intent.
Ensure critical actions like payments or sensitive updates require explicit user confirmation. For instance, a second confirmation page or two-factor authentication can act as a safeguard.
Clickjacking is more than a nuisance—it’s a serious cybersecurity threat that can compromise your privacy, reputation, and finances. By learning how it works and taking proactive steps, you can protect yourself and others.
Whether you’re a casual internet user or a professional developer, understanding the mechanisms behind clickjacking equips you with the tools to identify and prevent it.
In today’s interconnected world, protecting your data is essential. Clickjacking is a deceptive but preventable attack. By staying vigilant and applying the strategies in this guide, you can confidently navigate the online space while safeguarding your data.
Remember, the best defense against any cyberattack is knowledge. Share this guide with friends and colleagues to spread awareness about clickjacking and ensure a safer internet experience for everyone.